Access to the System
The access to Calendula is done using the SSH Secure Shell protocol. This protocol is used for access to remote machines over a network. It allows remote work through a command interpreter, but also allows redirecting traffic from the remote computer's graphics programs to the local computer's screen.
SSH uses encryption techniques that prevent third parties from accessing the content of communications. As it is a secure protocol, concepts such as public/private key or fingerprint, come into play. It is not the purpose of this manual to go into detail on these concepts but a brief description is necessary to fully understand the connection process and thus ensure the confidentiality of traffic between the user's system and the SCAYLE system.
Unique fingerprint or public key is an alphanumeric string of characters that identifies a specific server and serves to ensure that the server that is answering us is really the one we wanted to connect to.
To access the supercomputer we will use the URL calendula.scayle.es. Behind this address we find two different servers (called frontend11 and frontend12) that are in charge of handling login requests from remote users. This way, the number of simultaneous users accessing Calendula is distributed between both servers.
This solution poses an inconvenience, because the two servers have different public keys (although externally they respond to the same address), the first time we access, the key of one of the frontend is saved in the user's local machine and the following times, when we log in the other frontend, a security alert will appear warning the user of a possible attack of 'man-in-the-middle', since the public key of the other server is not stored.
To do this, we must save on our local machine the public keys of both frontend. Next you will learn how to save the keys on your local machine.
To access Calendula it is necessary to have an enabled user (provided by SCAYLE) and its respective password.
Users will need to generate public/private key pairs for each device/application they will use to access Calendula and transfer the generated public keys to gain access.
To access Calendula from Linux or macOS operating systems, the program is called Terminal.
For Windows operating systems, from SCAYLE we recommend the following programs to connect to our systems:
- PuTTY. It is a free, lightweight and very easy to install utility in any of the latest versions of Windows.
- MobaXterm. This tool is much more powerful than the previous one and includes multiple tools such as
SFTPbrowser, X11 server, etc. - Windows Subsystem for Linux. Compatibility layer created by Microsoft to run Linux natively on Windows. There are different Linux distributions that can be installed
(Ubuntu, OpenSUSE, Debian,...).
You will find in this manual a guide for the MobaXterm program. If in your case you use another program, you can find information in the manuals of the official developer or you can consult our GLPI system for any questions you may have.
In the following link “ecdsa_keys_calendula” you will find the keys of the two frontends. You can copy the content into the file $HOME/.ssh/known_hosts of your local machine or SSH connection program that you use to connect to Calendula.
In the following paragraph you will find the fingerprints of the two frontend:
Clave ECDSA frontend11. Formato MD5: e1:b4:0c:06:07:97:64:61:ca:94:fb:b7:95:b4:01:e2
Clave ECDSA frontend11. Formato SHA256: ENVK4Jkwgx1452ZXzho6kz9CDzAHu1nVwOve4tAWy1Q
Clave ECDSA frontend12. Formato MD5: 23:af:ce:0c:c3:f4:ef:43:37:da:e3:45:17:d3:87:e5
Clave ECDSA frontend12. Formato SHA256: zEDXH07QlixqR3sJ0jHb/n8c87NGX1sXF433R4iYgLEIn compliance with National Security Scheme, SCAYLE only accepts keys with the ECDSA signature algorithm and a NIST P-521 curve.
Next, you will learn how to upload your public key to Calendula in a secure and automated way. This process ensures that only authorized users can add keys to specific servers, maintaining the security and integrity of the system. We will use the ECDSA (Elliptic Curve Digital Signature Algorithm) algorithm with the NIST P-521 curve to generate and manage public keys.
In case you are in Windows you can select one of our guides for:
MobaXterm through this link: System access using MobaXterm. (MobaXterm is not available for macOS)
PuTTY through this link: System access using PuTTY.
First, you must obtain your public key in the proper format for the ECDSA algorithm using the NIST P-521 curve, known as ecdsa-sha2-nistp521.
If we are in a terminal or Linux command line emulator such as Terminal, iTerm2 (on macOS) the way to generate the public/private key pair is by using the command:
ssh-keygen -t ecdsa -b 521
It is recommended that you do not enter any password in the process of this command to avoid having to enter that password every time you log in..
This command will create the files in $HOME/.ssh:
id_ecdsa
id_ecdsa.pubThe file with id_ecdsa.pub will be the public key that you must transfer in the next point of the guide.
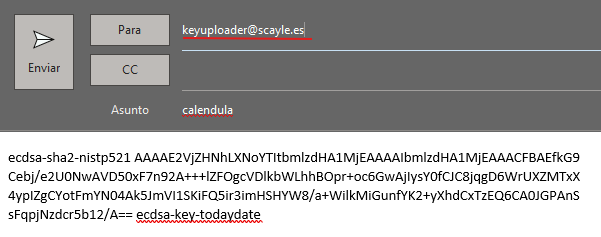
Then copy the contents of your public key id_ecdsa.pub and send an e-mail to the address with the subject "calendula" :
In the case of using file transfer programs to or from Calendula it is necessary to configure another public/private key pair for each program, such as Filezilla, WinSCP, CyberDuck or Bitvise.
The new key pairs that you generate must be sent to SCAYLE as you did in start of Step 2.
We recommend that you consult the official developer's manual of the program of your choice or in case of difficulty, you can get in contact with SCAYLE support team through the GLPI system for assistance.
After sending the mail, you will receive a response from the server indicating the status of the process. The possible results are:
SUCCESS:
- Confirmation: Public key successfully added.
FAILURE:
- Error: The connection to the server has failed. Please try again after a while. If the error persists, please contact through our system GLPI.
- Error: Incorrect public key. Make sure that the public key format is correct and that the body of the email contains only the public key text, no signatures or salutations.
- Error: Incorrect subject line. Make sure that the subject of the email is “calendula”.
NOTHING:
- If you do not receive any email, make sure that the sender email is the one linked to SCAYLE, as only these emails will be accepted to access the cluster. Please also check the spam folder of
your email program. If you still do not receive confirmation, please contact through our system GLPI.
To access from Windows, with a SSH connection program such as MobaXterm the configuration values for access to Calendula are as follows:
Host Name (or IP address): calendula.scayle.es
Port: 22
Connection type: ssh
To connect from Linux / macOS to Calendula, it is only necessary to enter the following command in the Terminal program:
ssh We will be asked for our user's password and we will log in.
As with the connection via the Windows tools, access via SSH checks that the public key of the system to which you are connecting matches the one you have stored. To avoid the security warning, you must copy the system frontend keys to the file, as you learned in the frontend public keys section.
-
When entering the password into the system, it is important to note that, no symbols of any kind will appear on the screen
(*, #, ...).
This is to prevent an outside observer from getting an indication of the length of the password entered. -
Once you have connected to our system, you enter one of the two login nodes (frontend) from which you can _transfer data, edit your job submission scripts, work with the file system, etc._.
-
If you encounter any problems related to updating the public access keys, we recommend that inside your $HOME/.ssh/ directory you should create a file named config with the following content:
UpdateHostKeys noWith the following line you would get to the same point without needing to create the config file:
ssh -o UpdateHostKeys=noIMPORTANT: No computational activity is allowed on these nodes. Keep in mind that these are shared servers between all users and activities that demand a large amount of memory or CPU time, will harm the work of the rest of the users. Therefore, there are limits set on the CPU time and the number of processes that a user can open.
Once you have successfully completed the process you will have access to your $HOME directory on the Calendula supercomputer.
Last update: 30/07/2025 10:21